26
Aug
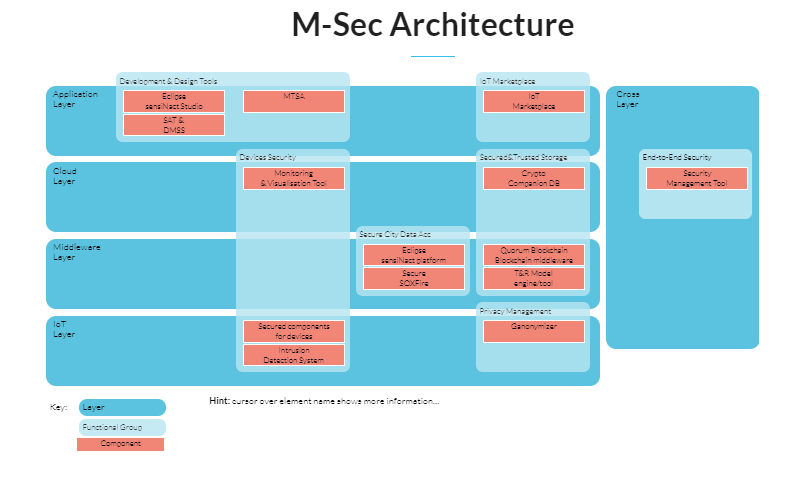
Simplified view of M-Sec architecture
Application
Layer
Layer
Application layer defines all the use the IoT technology or in
which IoT has deployed
which IoT has deployed
Eclipse
sensiNact Studio
sensiNact Studio
Eclipse sensiNact Studio
SensiNact is designed to allow platforms to interoperate, thus coexist and benefit from the richness of the variety. Additionally, it provides a fine grained security mechanism to allow access to services by only authenticated and authorized entities
SensiNact is designed to allow platforms to interoperate, thus coexist and benefit from the richness of the variety. Additionally, it provides a fine grained security mechanism to allow access to services by only authenticated and authorized entities
SAT &
DMSS
DMSS
Security Analysis Tool & Development Method for a secure service A security requirements modelling support system, for a misuse case diagram that enables the association of security knowledge with elements that constitute the diagram.
MTSA
Modal Transition System Analyser A development tool for synthesizing behaviour specification for reactive systems with formal guarantee.
IoT
Marketplace
Marketplace
IoT Marketplace The M-Sec IoT Marketplace is a novel Marketplace where smart objects and users can exchange information and services through the use of virtual currencies, allowing real-time matching of supply and demand, and thus enabling the creation of liquid markets with profitable business models of the IoT stakeholders.
Cloud
Layer
Layer
Cloud layer includes all the infrastructure upon which cloud services are based
Monitoring
& Visualisation Tool
& Visualisation Tool
Monitoring & Visualisation Tool A software-based solution that collects and examines activity from IoT layer or agents embedded in the IoT gateway devices. This tool not only help with the security health checks by providing insight into how the security is being maintained at IoT gateways, but also helps in further analysis of devices under attack. Thereby, providing 24/7 security threat monitoring and alerts.
Crypto
Companion DB
Companion DB
Crypto Companion Database> As the real world matches the digital world, ensuring that information remains secure, private and authentic has become an ongoing challenge. Using blockchain technology, some of the issues can be addressed. However, once data is stored on the blockchain it can’t be manipulated or altered. Our companion database is proposed as a parallel system to the blockchain for the encrypted storage. The blockchain saves a hash created from sensitive or personal data, and the companion database stores the sensitive data encrypted together with the hash.
Middleware
Layer
Layer
Middleware layer includes the infrastructure needed for both Peer-to-Peer and IoT-to-Cloud approaches
Eclipse
sensiNact platform
sensiNact platform
Eclipse sensiNact platform SensiNact is designed to allow platforms to interoperate, thus coexist and benefit from the richness of the variety. Additionally, it provides a fine grained security mechanism to allow access to services by only authenticated and authorized entities.
Secure
SOXFire
SOXFire
Secure SOXFire SOXFire can provide practical distributed and federated infrastructure for IoT sensor data sharing among various users/organisations in a way that is scalable, extensible, easy to use and secure, while preserving privacy.
Quorum Blockchain
Blockchain middleware
Blockchain middleware
Quorum Blockchain Blockchain middleware A distributed ledger and middleware services system which provides all the necessary groundwork for security/privacy-enhancing services related to transactions and interactions between actors of various ecosystems.
T&R Model
engine/tool
engine/tool
Trust & Reputation Model/Engine The Trust & Reputation
Management Engine (T&RM Engine) is a tool working on top of the M-Sec
blockchain/Marketplace and in parallel with the corresponding
middleware so as to provide a ranking system assessing the
reliability, trustworthiness and reputation of resources providers
within the MSec ecosystem.
Management Engine (T&RM Engine) is a tool working on top of the M-Sec
blockchain/Marketplace and in parallel with the corresponding
middleware so as to provide a ranking system assessing the
reliability, trustworthiness and reputation of resources providers
within the MSec ecosystem.
IoT
Layer
Layer
IoT Layer includes all the devices, sensors, and their
corresponding low-level networks that are met in IoT ecosystems
corresponding low-level networks that are met in IoT ecosystems
Secured components
for devices
for devices
Secured components for devices A secure element, such as a
TPM, is added to the physical platform, It is used to store any
sensitive information that shall be protected from people having
physical Access to the electronics, such as IoT devices and gateways.
The secure element handles the integrity of the device during the
boot process and also handles the authentication and encryption for
external communication channels.
TPM, is added to the physical platform, It is used to store any
sensitive information that shall be protected from people having
physical Access to the electronics, such as IoT devices and gateways.
The secure element handles the integrity of the device during the
boot process and also handles the authentication and encryption for
external communication channels.
Intrusion
Detection System
Detection System
Intrusion Detection System Protect vulnerable IoT devices from
malicious activities using defense-in-depth mechanisms and threat
monitoring, thereby providing multi-layered security against policy
violations and cyber attacks, along with security health-checks
malicious activities using defense-in-depth mechanisms and threat
monitoring, thereby providing multi-layered security against policy
violations and cyber attacks, along with security health-checks
Ganonymizer
GanonymizerIn situations where video data is used in various
IoT application use cases such as smart cities, personal information
is often a problem. GANonymizer is a technology that automatically
deletes personal information contained in such videos using AI
technology.
IoT application use cases such as smart cities, personal information
is often a problem. GANonymizer is a technology that automatically
deletes personal information contained in such videos using AI
technology.
Cross
Layer
Layer
Cross layer is the layer that provides services to all the horizontal layers.
Security
Management Tool
Management Tool
Security Management Tool A set of centralized security
functions that are necessary to ensure end-to-end security, privacy
and therefore digital trust. It is designed to support several
security functionalities aggregated in a single backend using the
LDAP standard. The central element for the security manager is a
directory service containing all information to manage security
services for clients, such services known as AAA for Authentication,
Accounting and Authorization.
functions that are necessary to ensure end-to-end security, privacy
and therefore digital trust. It is designed to support several
security functionalities aggregated in a single backend using the
LDAP standard. The central element for the security manager is a
directory service containing all information to manage security
services for clients, such services known as AAA for Authentication,
Accounting and Authorization.
Development & Design Tools
Development & Design Tools Functional Group …
Devices Security
Devices Security Functional Group…
Secure City Data Acc
Secure City Data Access Functional Group…
IoT Marketplace
IoT Marketplace Functional Group…
Secured&Trusted Storage
Secured & Trusted Storage Functional Group…
Privacy Management
Privacy Management Functional Group…
End-to-End Security
End-to-End Security FG…
End-to-End Security
End-to-End Security FG…
Key:
Layer
Layered Layered architecture patterns are n-tiered patterns
where the components are organized in horizontal layers. This is the
traditional method for designing most software and is meant to be
self-independent. This means that all the components are
interconnected but do not depend on each other.
where the components are organized in horizontal layers. This is the
traditional method for designing most software and is meant to be
self-independent. This means that all the components are
interconnected but do not depend on each other.
Functional Group
Functional Groups represents a reusable, functional, identifiable part of the
whole framework that provides a set of functionalities based on the combination of other components.
whole framework that provides a set of functionalities based on the combination of other components.
Component
Component represents a smaller functional part that in a combination with other components,
introduce the functional group component. A component is an self-contained software which can
communicate with other components. In this representation a component can also represent a set of components. We are not representing interfaces and connectors.
introduce the functional group component. A component is an self-contained software which can
communicate with other components. In this representation a component can also represent a set of components. We are not representing interfaces and connectors.
Hint: cursor over element name shows more information…